This Item Ships For Free!
Spring boot application security top
Spring boot application security top, 10 Excellent Ways to Secure Your Spring Boot Application Okta top
4.84
Spring boot application security top
Best useBest Use Learn More
All AroundAll Around
Max CushionMax Cushion
SurfaceSurface Learn More
Roads & PavementRoads & Pavement
StabilityStability Learn More
Neutral
Stable
CushioningCushioning Learn More
Barefoot
Minimal
Low
Medium
High
Maximal
Product Details:
Product code: Spring boot application security topGetting started with Spring Security and Spring Boot top, How does Spring Security work internally by Haytam Benayed top, Architecting Spring 5 Applications Spring Security and Its Architectural Design packtpub top, Spring boot security authentication examples top, 10 Excellent Ways to Secure Your Spring Boot Application Okta top, Spring Boot Token based Authentication with Spring Security JWT top, Form Login Spring Security top, Understand Spring Security Architecture and implement Spring Boot top, Basic Authentication Spring Security top, Spring Security Reference top, Top 10 Courses to Learn Spring Security OAuth2 and JWT with top, Spring Boot Security Default Configuration MVP Java top, How to Configure CORS in a Spring Boot Spring Security top, Spring Security Architecture GeeksforGeeks top, What is Spring security Java Development Journal top, Getting Started Spring Security and Angular top, Registration and Login with Spring Boot Spring Security top, Spring Boot 2 JWT Authentication with Spring Security BezKoder top, Spring security architecture diagram W3schools top, Understand Spring Security Architecture and implement Spring Boot top, Spring Security architecture Hyperskill top, Architecture Spring Security top, Spring Boot 3 Spring Security 6 In Depth Understanding by top, Spring Security Authentication Success Handler Examples top, Explain Spring Security architecture and working top, How To Implement Security In Spring Boot Project JavaTechOnline top, Spring Security JWT Tutorial Toptal top, 10 Spring Boot security best practices Snyk top, Spring Boot Web Application Part 5 Spring Security Spring top, JWT Authorization with Spring Boot 3 Spring Security 6 2024 top, Spring Security Form Login with Database top, Spring Security UserDetailsService Using Spring Boot 3 top, Web Security Training with Spring Boot inovex GmbH top, Spring Boot application using Spring Security and a MySQL database top, Spring Security Reference top, 10 Excellent Ways to Secure Your Spring Boot Application Okta top, Spring Boot Spring Security JWT MySQL Database Tutorial top, Secure Spring Boot Apps with YugabyteDB and Secret Manager Services top, Spring Security Login Java Development Journal top, How To Implement Security In Spring Boot Project top, Stateless API Security with Spring Boot Part 1 InSource Software top, Spring Security Architecture Big Picture Part1 top, Spring Security Before Authentication Filter Examples top, java User class for Spring Security application Stack Overflow top, Secure Spring Boot Apps with YugabyteDB and Secret Manager Services top, How to use PreAuthorize annotation in a spring boot application top, Spring Security Java Configuration Annotation Example Dinesh on Java top, Spring Security Registration and Login Application Tutorial 2023 top, Spring Security Reference top, Spring Boot Security JWT Hello World Example JavaInUse top.
- Increased inherent stability
- Smooth transitions
- All day comfort
Model Number: SKU#7381235
Specs & Fit
Spring boot application security top
How It Fits
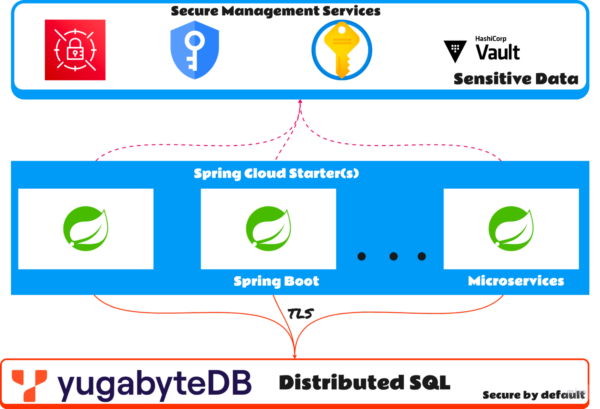
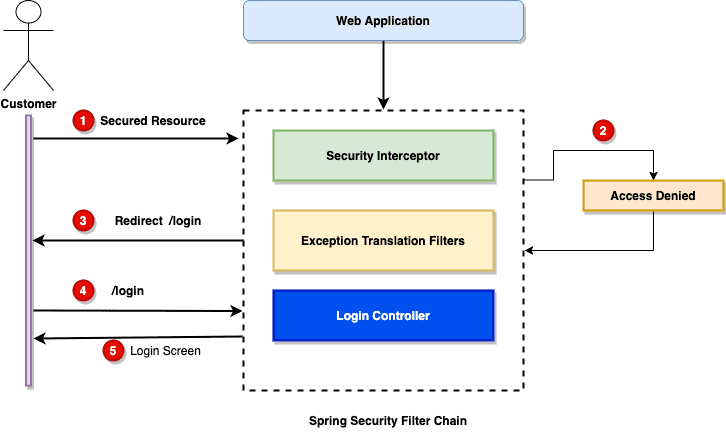
Stateless API Security with Spring Boot Part 1 InSource Software- spring boot application security
- spring boot application with hibernate
- spring boot application with mongodb example
- spring boot application with jpa example
- spring boot application with mongodb
- spring boot application with oracle database example
- spring boot application with reactjs
- spring boot architecture
- spring boot architecture flow
- spring boot architecture example